Nebulaworks Insight Content Card Background - Bernard hermant belgium metal
Recent Updates
As Kubernetes matures and becomes more widely adopted in the enterprise, the requirements for advanced authorization policies are needed. Gone are the days of the easy button and using out-of-the-box RBAC authorization to meet the increasing demands of the business and its end users.
Why use Open Policy Agent?
If your organization has made the commitment to utilize platforms such as Kubernetes for their enterprise microservices orchestration, it wasn’t because they wanted to use the latest and greatest technology. It was because the business required a faster, more nimble approach to getting their applications to the end consumers in a highly available automated fashion. When architecting authorization for services in a Kubernetes cluster, you have to take the following into consideration:
- SECURITY
- Transactions
- Triggers
- Policy Syntax
- Policy Compliers
- Interactive Queries
- Did I mention SECURITY
Each of these items needs to be designed, implemented, and tested independently as well as together to ensure the proper behavior as well as an overall positive experience for the end users!
With Open Policy Agent, all of the above is handled for you in a secure, easy-to-deploy, open-source manner for any service!
How does Open Policy Agent work?
All of Open Policy Agent’s REST APIs utilize JSON over HTTP so it can be integrated with all programming languages!
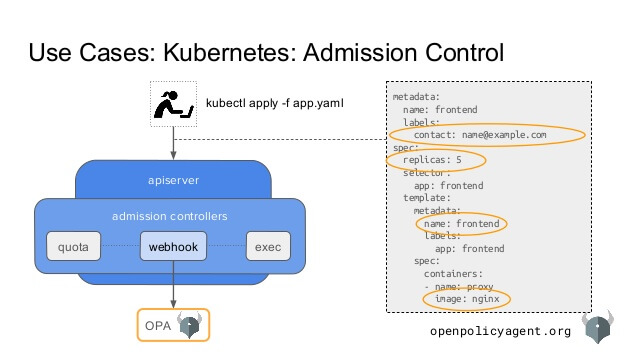
When using Open Policy Agent with Kubernetes, the following steps happen when an authentication and authorization request is made:
Request is received by Kubernetes authentication module within the API server.
If the request is authorized, it is forwarded to authorization module.
- simple authz (authorization) is handled by RBAC based on permissions.
The request is then forwarded to the webhook within the authz module.
- Based on user information that is extracted from the request, advanced permissions are applied and returned.
With some specific requests, once authentication is complete, the request can forward directly to another module within the Administration Controllers module on the API server. When this happens, a mutated webhook is invoked and authn is handled directly by Open Policy Agent.
When should you start considering Open Policy Agent for your authorization needs for your Kubernetes environments?
As you have read thus far, you need to consider Open Policy Agent early in the architecture design phase. Not only will it enable you to have tighter integrated authorization policy management, but it also saves your organization an immense amount of time in the entire design, test, and release lifecycle.
Here at Nebulaworks, we can guide and assist you in all phases of your Kubernetes architecture, even if you have an existing environment. With our expertise in open-source technologies and how enterprises can adopt them, we can help accelerate your organizations maturity in the rapidly changing world of micro services. When you are ready to take the next step in your evolution of digital transformation, reach out to us.

Looking for a partner with engineering prowess? We got you.
Learn how we've helped companies like yours.






